Lastline Products Overview

A universal detection method for advanced malware across critical applications.
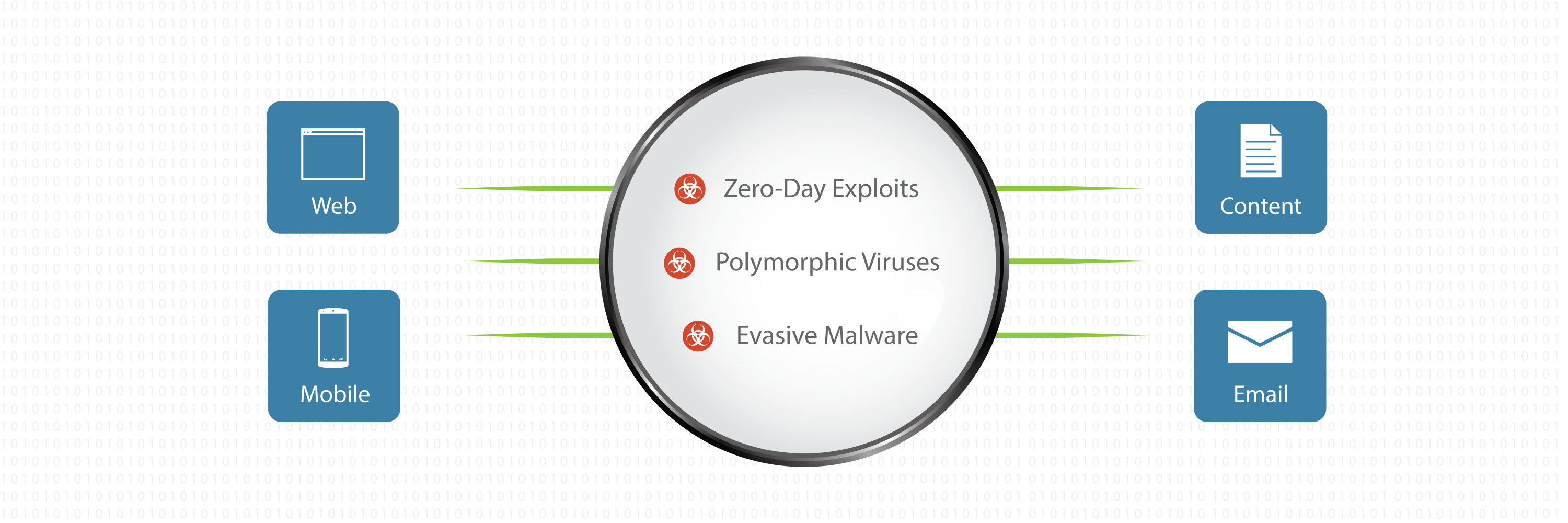
High-Resolution Security Analysis
for web, email, content, and mobile apps, Lastline’s full-system emulation functionality dissects not only APTs, but malware crafted to evade detection by traditional sandboxes used by first-generation APT security vendors.
Global Threat Intelligence
be aware of the latest advanced threats, Lastline crawls the web utilizing emulated browsers, machine learning, information on objects analyzed and big data analytics to build a knowledge base of malicious objects, bad IP addresses and active command-and-control systems.
Distributed Architecture That Scales
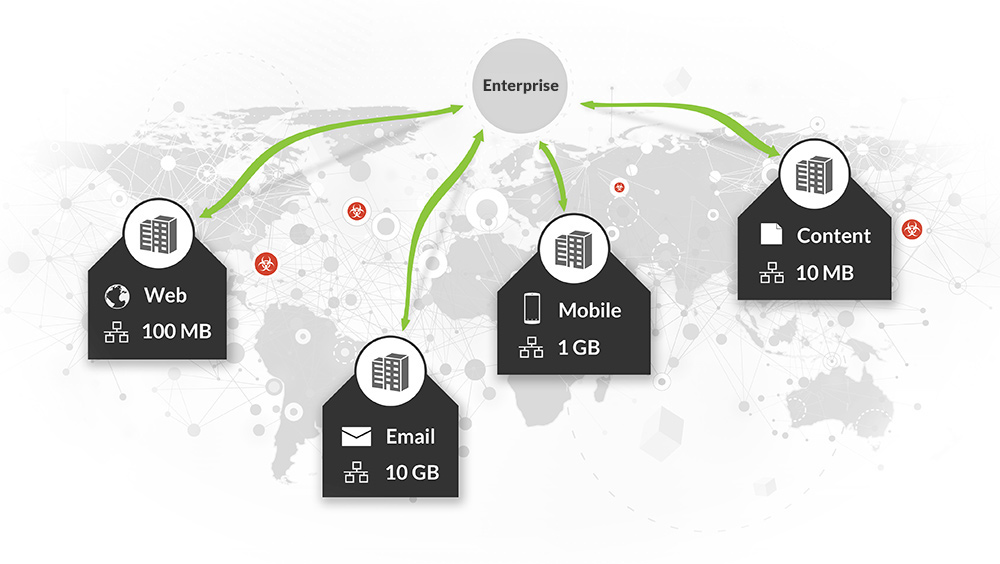
throughout your entire network, Flexible architecture allows for easy scalability as your architectural, operational and business needs change. We offer organizations the ability to deploy on commodity hardware or in virtual environments on a per-user basis, so go ahead, deploy as much as you'd like. Expensive proprietary hardware is a thing of the past.
Actionable Threat Intelligence
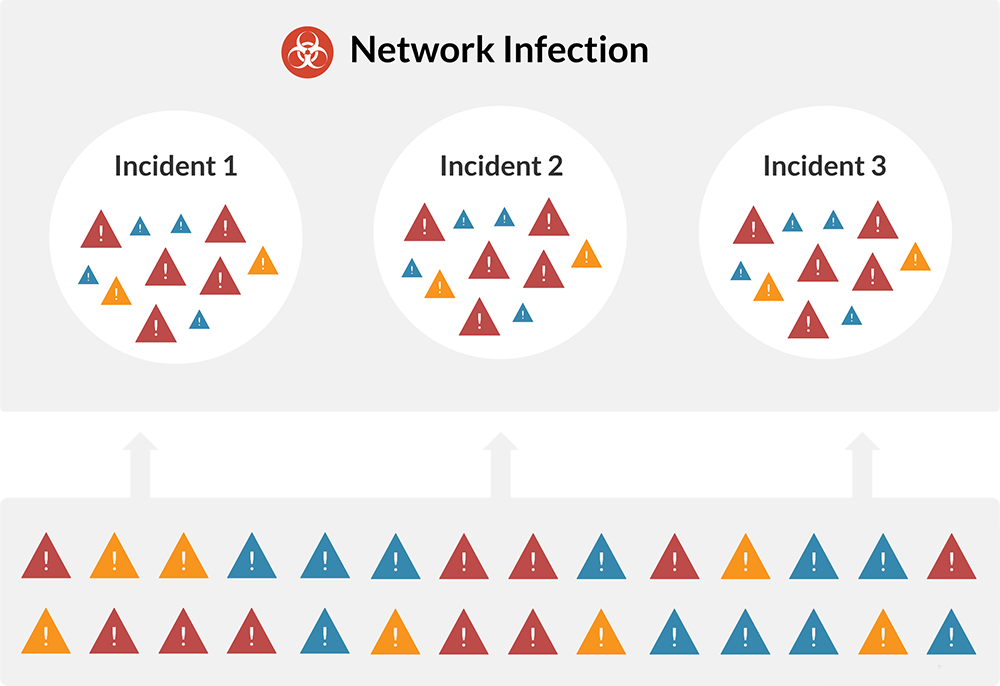
more signal, less noise, When a threat is serious, you will know. Lastline makes it easy for you to identify critical APTs targeting your network. Network activity is correlated with information resulting from the execution of software artifacts, providing an incident-centric view of infections. The ability to link together the various steps involved in the compromise of an internal endpoint supports root-cause analysis and more effective remediation.
Integrate With Traditional Security Systems
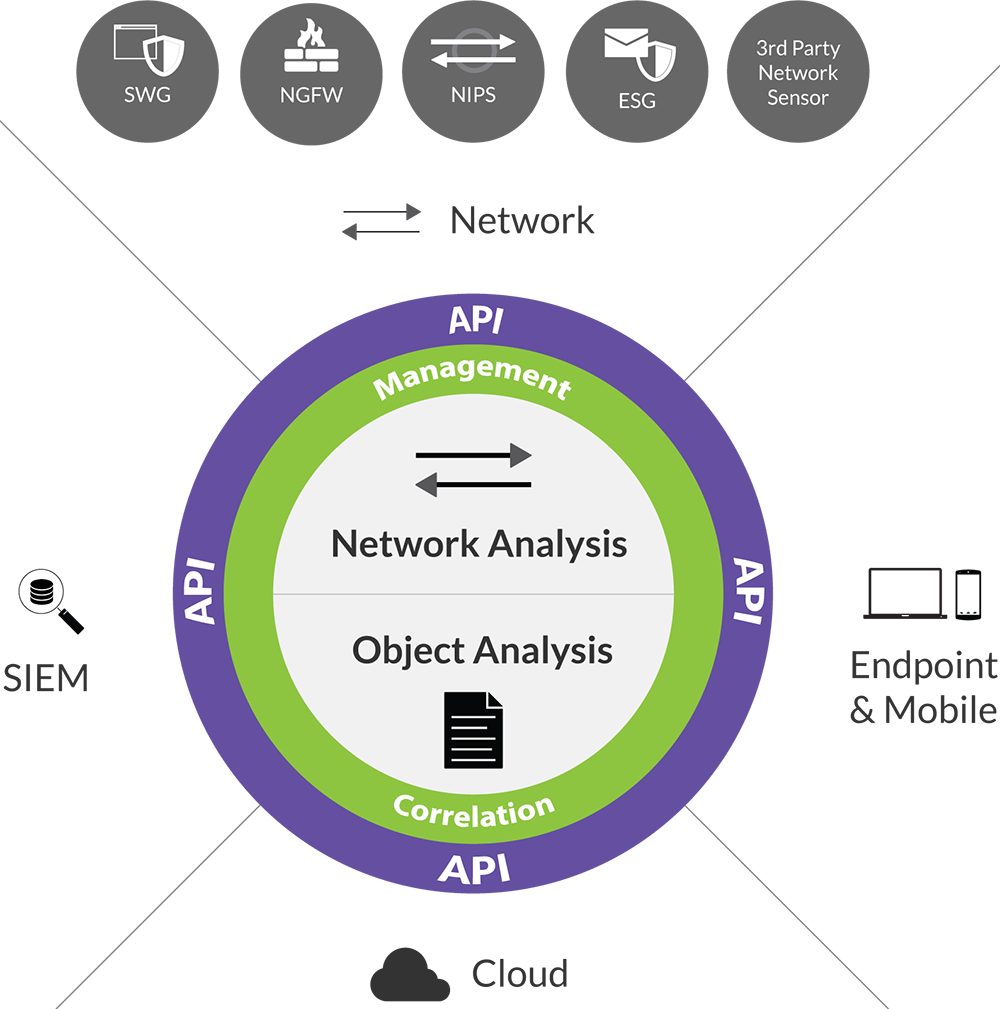
and complement other defense countermeasures, Lastline's unrivaled API capabilities allow you to easily integrate our software solution with existing security infrastructures to add malware analysis and better protect against advanced cyber threats. Use your own sensors or existing technologies — SWGs (Secure Web Gateways), IPSs (Intrusion Protection System), NGFWs (Next-Generation Firewalls) and SIEM (Security Information Event Management) installations can all interoperate seamlessly with Lastline Enterprise.
Deploy in your private cloud or ours
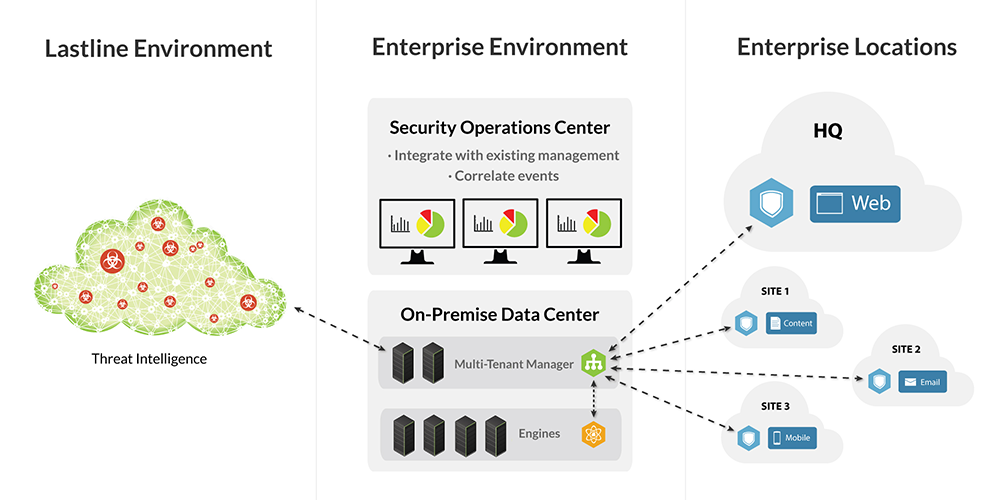
because everyone loves options, Lastline Enterprise was designed with flexibility in mind. If your Enterprise is restricted by strict privacy laws and policies, deploy on-premise, and install components in your data center. Network behavior models associated with malware will be regularly downloaded from Lastline. Or choose the hosted deployment model and Lastline will manage the backend infrastructure for you.












